
Next: Regret Up: 9.3 Two-Player Zero-Sum Games Previous: 9.3.1 Game Formulation
What constitutes a good solution to Formulation 9.7?
Consider the game from the perspective of
![]() . It seems reasonable
to apply worst-case analysis when trying to account for the action
that will be taken by
. It seems reasonable
to apply worst-case analysis when trying to account for the action
that will be taken by
![]() . This results in a choice that is
equivalent to assuming that
. This results in a choice that is
equivalent to assuming that
![]() is nature acting under the
nondeterministic model, as considered in Section 9.2.2.
For a matrix game, this is computed by first determining the maximum
cost over each row. Selecting the action that produces the minimum
among these represents the lowest cost that
is nature acting under the
nondeterministic model, as considered in Section 9.2.2.
For a matrix game, this is computed by first determining the maximum
cost over each row. Selecting the action that produces the minimum
among these represents the lowest cost that
![]() can guarantee for
itself. Let this selection be referred to as a security
strategy for
can guarantee for
itself. Let this selection be referred to as a security
strategy for
![]() .
.
For the matrix game in (9.42), the security strategy is illustrated as
This can be formalized using the existing notation. A security
strategy, ![]() , for
, for
![]() is defined in general as
is defined in general as
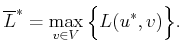 |
(9.45) |
Now swap roles, and consider the game from the perspective of
![]() ,
which would like to maximize
,
which would like to maximize ![]() . It can also use worst-case
analysis, which means that it would like to select an action that
guarantees a high cost, in spite of the action of
. It can also use worst-case
analysis, which means that it would like to select an action that
guarantees a high cost, in spite of the action of
![]() to potentially
reduce it. A security strategy,
to potentially
reduce it. A security strategy, ![]() , for
, for
![]() is defined as
is defined as
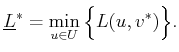 |
(9.47) |
An interesting relationship between the upper and lower values is that
![]() for any game using Formulation
9.7. This is shown by observing that
for any game using Formulation
9.7. This is shown by observing that
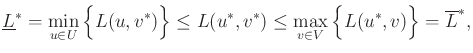 |
(9.49) |